The threshold to determine whether an incident affecting energy companies is reportable has prevented any reports being made.
A cyber security law introduced three years ago was meant to boost the resilience of the UK's energy sector by obliging gas and electricity firms to report when they were hacked.
But since then not a single report has been made, Sky News can reveal, despite numerous successful hacks of British energy firms attributed to hostile states as well as criminal groups.
Ofgem, the authority that is meant to receive these reports, told Sky News that only one company has ever tried to file a report informing the regulator that it had been hacked, but they were dismissed as the incident did not meet the threshold for being reported.
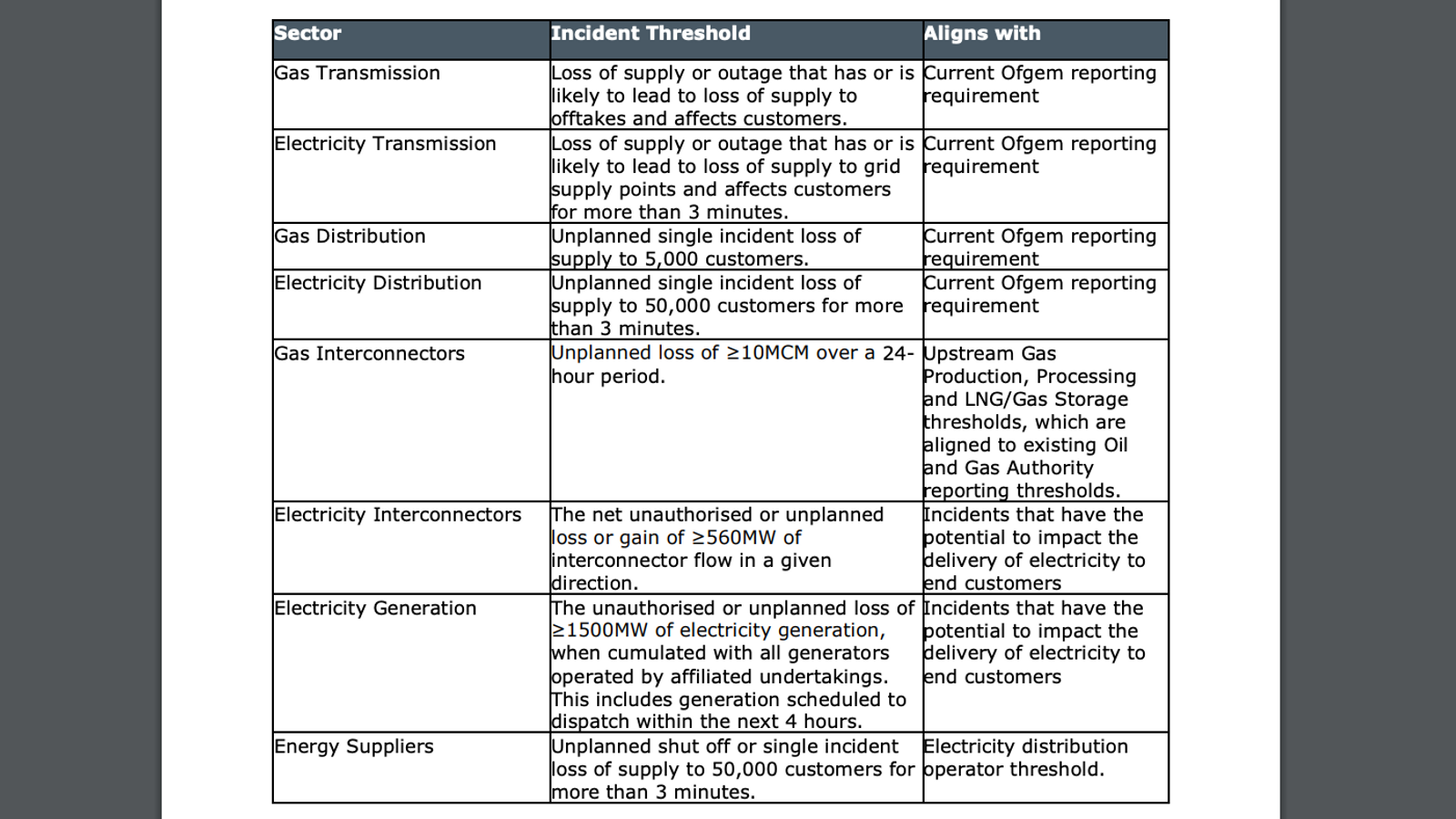 Ofcom's incident thresholds are based on the impact of an attack on customers
Ofcom's incident thresholds are based on the impact of an attack on customers
Last year, staff at a little-known company called Elexon - a firm that plays a critical role in balancing and settling payments between power plants and electricity suppliers - was left locked out of its internal systems due to a ransomware attack.
The British government has confirmed that Russian state-sponsored hackers have successfully penetrated the computer networks of the UK's energy grids, without disrupting them.
Former defence secretary Gavin Williamson warned that "thousands and thousands and thousands" of people could be killed if an attempt at disruption was made.
But the high thresholds for companies working across the gas and electricity sectors to report cyber security incidents to Ofgem risks leaving the regulator blind to how the sector is actually coping in the face of these threats.
These thresholds are based on the impact of hacks to the continuity of the companies' services, a metric that does not record the sector's security capabilities, just the intentions of the attackers.
Dr Jamie Collier, a threat intelligence consultant at FireEye, told Sky News that the thresholds could be useful considering the varying levels of sophistication across attacks on critical infrastructure organisations, allowing defenders to "focus on what really matters".
But the cyber security expert added: "Despite this, essential service providers and regulators should be careful not to neglect the threat posed from less sophisticated attacks."
FireEye has detected an increase in critical infrastructure incidents caused by novice hackers due to the growing availability of tools enabling these hackers to interact with industrial control systems.
The company also warns that multiple, highly-prolific criminal organisations with a financial motivation are currently "active inside essential service provider networks with the intent of profiting from a ransom of stolen information and disrupted services".
 FireEye warns that novice hackers are now targeting industrial control systems.
FireEye warns that novice hackers are now targeting industrial control systems.
"Most of the concern around cyber security has been focused on operational technology (OT) networks that interact with physical processes and machinery, such as power plant equipment or water treatment facilities," Dr Collier explained.
"Yet the traditional information technology (IT) networks that involve the flow of data - such as file storage or email - should not be neglected. This is because whilst the impact of malicious activity can be far more severe against OT systems, these attacks typically start out on IT networks. It is therefore vital to consider security across an entire service provider's infrastructure."
Dr Collier stressed that critical infrastructure providers "deserve credit for their use of fail-safe mechanisms that can mitigate the destructive impacts of many attacks".
Responding to Sky News, a government spokesperson said: "The UK's critical infrastructure is extremely well protected and over the past five years we have invested £1.9bn in the National Cyber Security Strategy to ensure our systems remain secure and reliable."
They added that a formal review of the impact of the cyber security law, the Network & Information Systems Regulations, will take place within the next 12 months.















